The rapid development of communication networks, especially the Internet, has caused widespread concern in information security. In the information security algorithm, the advantages of the RSA method are mainly that the principle is simple and easy to use. However, with the improvement of the method of decomposing large integers, the improvement of computer speed and the development of computer networks, the requirements for large integers for RSA encryption and decryption security are increasing. In order to ensure the security of RSA, the number of keys is increasing. It is generally considered that RSA needs more than 1024 words to have security. However, the increase in the length of the key leads to a significant reduction in the speed of encryption and decryption, and the hardware implementation becomes more and more complex, which imposes a great burden on the application using RSA (especially e-commerce for a large number of secure transactions). As a result, its application range is increasingly restricted.
The ECC algorithm can achieve the same encryption strength as the RSA algorithm with a short key. Its number theory is based on the elliptic curve discrete logarithm problem on the finite field. There is no sub-exponential time algorithm for this problem. The ECC algorithm has the highest security strength per bit. Since the smart card is limited in CPU processing power and RAM size, it is very important to implement a digital signature application by using a public key cryptosystem with small computational complexity and high encryption strength. ECC has obvious advantages in this respect. The security of the 160-bit ECC algorithm is equivalent to the 1024-bit RSA algorithm, and the 210-bit ECC is equivalent to the 2048-bit RSA. It is believed that the application of ECC technology in the field of information security will become more and more extensive.
At present, many smart card/USB Key chip manufacturers have implemented ECC-enabled public key cryptographic hardware coprocessors on their products. For example, NXP's smart card chip can implement 192-bit ECC digital signature operation within 40ms; some STMicroelectronics products facilitate the implementation of RSA and ECC algorithms through coprocessors and fast multiply and accumulate instructions; Infineon The SLE66CxxP can accelerate the processing of public key cryptographic algorithms such as RSA and ECC through a hardware modulo operation unit; Atmel's AT90SC19264RC and AT91SC25672RC products also implement hardware coprocessors for public key cryptography. In terms of high-performance authentication and encryption chips: Siemens' PLUTO-IC is a high-performance encryption chip based on the GF(p) domain curve ECC algorithm. The ECC has a die length of 320 bits; ELCRODAT-6-2 is a type of The encryption chip of the ISDN communication network is also based on the ECC algorithm of the GF(p) domain curve, and the ECC has a modulus of 256 bits.
There are also a large number of chips using ECC technology in China, among which the more influential are the smart card/USB Key chip of Beijing Zhongdian Huada Electronic Design Co., Ltd. and Shenzhen Zhongxing IC Design Co., Ltd., Beijing Huada Xinan Technology Co., Ltd. The high-performance ECC chip series, etc., all support ECC national standard algorithms and a variety of ECC international standard algorithms.
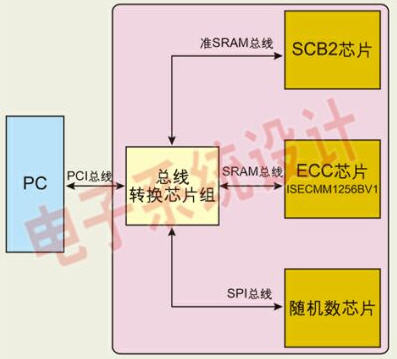
System block diagram of an encryption card based on ECC cipher chipset
The ISECMM1256BV1 security chip is an ECC algorithm chip introduced by Beijing Huada Xinan Technology Co., Ltd. to solve the problems in the current information security product design process. The chip is an efficient and universal public key crypto chip. It implements ECC national standard algorithm, ECC international standard algorithm and RSA algorithm from hardware. It also implements some Hash standard algorithms, including Hash national standard algorithm (also known as SM3). Password hash algorithm), SHA-1 and SHA-256. The ECC key pair can also be stored in a chip with a Flash memory area for storing and managing up to 64 pairs of ECC key pairs, which is called a "key pool." Only authorized users can obtain the operation rights of the ECC key pair in the key pool. To protect the security of the ECC private key in the key pool, the SCE implementation of the chip incorporates the Side Channel Attack (SCA) technology to enhance the protection of the private key in the key pool.
In the application of the chip, since the transmission rate of the PCI bus has great advantages in the external interface of the PC, the current encryption card selects the PCI bus to communicate with the PC. Figure 1 shows the basic platform of the PCI encryption card based on the Huada Principal ECC cipher chip ISECMM1256BV1. The PCI bus is converted into the SRAM bus, the quasi SRAM bus and the SPI bus by the bus conversion chipset. The PC achieves the purpose of separately accessing each chip by providing different base addresses to the PCI bus, and is very convenient to apply. The ISECMM1256BV1 security chip contains a CPU inside, and the ECC algorithm engine is packaged by embedding code. Therefore, there is no need to care about ECC algorithm implementation and protocol implementation in the application process. This encryption card allows the PC to directly access the ISECMM1256BV1 chip through the bus conversion chipset to meet the needs of ECC and RSA algorithm applications. In addition, a random number chip and an SCB2 chip are added to the board, and various operation modes such as ECB, CBC, and OFB are added, and the application range of the encryption card is expanded. As the basic mode of the encryption card, the cryptographic algorithm chip required by the user can be arbitrarily expanded on the basis of the scheme, and the function of the card is expanded to meet the different needs of the user. Based on this scheme, applications such as ECC algorithm, RSA algorithm and SCB2 algorithm can be easily implemented to protect information security.
Author: Hou Hongfei Email:
Beijing Huada Xinan Technology Co., Ltd.
1. 3D Shaped Transport Eraser Wherever you want,you
need transport,that's is why we have Transport Shaped Eraser.Our 3D
shaped transport eraser have various styles,for big one,we have 3D tank
shaped eraser, 3D ambulance shaped eraser, 3D airplane shaped eraser,for
small one,we have 3D motorbike shaped eraser, 3D helicopter shaped
eraser,so many shapes ,so many colors,just wait for you.

2. Mould Analytical diagram
A detailed diagram of the disassembled , easy to your understanding our 3D Panda Shaped Erasers

3. Eraser color
When you first look at our transport eraser,you will be suprised by
it's bright,like 3D red forklift shaped eraser, 3D yellow forklift
shaped eraser,and some others,as 3D pink tank eraser, 3D blue
helicopter eraser,all the colors will make you happy.

Transport Shaped Eraser
Fun Shaped Erasers, Novelty Erasers, Transport Eraser
Yiwu Soododo Stationery Co., Ltd , https://www.toy-eraser.com