1. Foreword
In recent years, the smart card market has shown a trend of increasing geometric progression. With their unique security and reliability, smart cards are widely used in security solutions from single devices to large complex systems. However, with the increasing popularity of smart cards. Various specialized attack technologies for smart cards are also evolving. Analyze the security attacks faced by smart cards and study the corresponding prevention strategies, which is of great significance for ensuring the security of the entire smart card application system.
2. Smart card attack technology is busy and its strategy
Attacks on smart cards can be divided into three basic types: physical attacks, edge-frequency attacks, and failure analysis attacks. The following is an analysis of the specific implementation of these three attack techniques.
2.1 Physical Attack
Although all the functions of the smart card seem to be enclosed in a single chip, it is still possible to reverse engineer it. The main methods used to implement physical attacks include:
(1) Microprobe technology: The attacker usually restores the electrical connection between the chip function pad and the outside after removing the chip package, and finally can use the micro probe to acquire the signal of interest (Fig. 1), thereby analyzing the smart card. Regarding the design information and the storage structure, even the information of the memory is directly read and analyzed.
All Infineon smart card chips provide a strong anti-snag mechanism that covers the entire chip with complex CPU-controlled active shielding technology. Once the chip is spy, it is necessary to destroy or interfere with the normal function of the active shielding layer, then the CPU can instantly detect the alarm signal sent by the active shielding layer, and adopt different levels of active defense measures according to the COS setting. The new generation of chips uses a proprietary multi-layer layout structure. This is equivalent to adding a separate active layer to each layer of the circuit. There is currently no precedent for using probe technology (physical attacks) to crack Infineon chips.

Figure 1 chip probe station
(2) Layout reconstruction: Using high-power optics and radio microscopy to study the connection mode of the circuit, it can quickly identify some basic structures on the chip, such as data lines and address lines. Infineon's smart card chip uses encrypted memory design (MED). All types of memory RAM, ROM, EEPROM, FLASH and other stored information are processed through a special encryption mechanism. The result is that even if the stored content is attacked. The illegal acquisition, these encrypted information is also meaningless to the attacker. Moreover, the probability of being directly read by an attacker is extremely low. It is worth mentioning that this encrypted memory design is invisible to the user and is physically implemented. Developers do not need to consider the encryption and decryption of stored content, and will not impose an additional burden on developers.
Physical attacks are powerful means of achieving successful detection, but their disadvantage is the intrusive attack mode. At the same time, expensive high-end laboratory equipment and specialized detection technology are required. The key to dealing with physical attacks is to increase the complexity of chip design and the fineness of chip manufacturing. Infineon's new generation of smart card controllers are used. 13urn's design process.
2 2 edge frequency attack
Edge-frequency attacks analyze the encrypted data of smart cards by observing the changes in certain physical quantities such as energy consumption, electromagnetic radiation, time, etc. in the circuit. The edge frequency attack method mainly includes the following methods:
(1) DPA (Diferential Power Analysis. Differential Energy Analysis 1DPA attack is to detect the behavior of the electronic device by using the oscilloscope to detect its energy consumption (Figure 2). The basis of the DPA attack is to assume the data and energy consumption of the processed data. There is a connection, that is, assuming that the energy used by 0 to 1 is different, then the two energy trajectories that perform the same algorithm on two different data will have a slight difference due to the difference of the input data, that is, the differential trajectory. That is, the clock cycle in which the input data produces a difference. By checking all the inputs of the encryption algorithm and the differential trajectories generated by each pair of 0's and 1's, it is possible to identify the exact time they appear in the program code to obtain the encryption key.
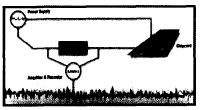
Figure 2 Schematic diagram of DPA
DPA enables the internal processing of encryption algorithms to be studied. In theory, all encryption algorithms can be cracked with DPA. In addition, the application of this attack method is very simple and requires only a small investment. Therefore, solving the DPA problem has become one of the most urgent problems for smart card manufacturers. Infineon's smart card chip is designed with a dual-track pre-charge logic to ensure data processing and energy consumption. And the internal bus is logically scrambled and irregular current processing, the possibility of DPA is completely eliminated from the hardware, and Infineon can provide a variety of customized software strategies for its users. This perfectly solves the problem of DPA attacks.
(2) DEMA: All electronic equipment will have electromagnetic radiation generated. Differential ElectroMagnetic Optical Analyses (DEMA) are similar to DPA, assuming that there is a relationship between the processed data and the amount of electromagnetic radiation (Figure 3).
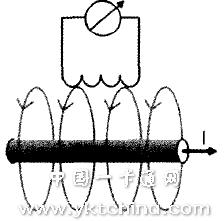
Figure 3 Schematic diagram of DEMA
In general, the signal-to-noise ratio of the signal and noise is compared. Differential electromagnetic attack (DEMA) yields better peaks than differential energy attack (DPA). Therefore, the signal-to-noise ratio of the electromagnetic signal is greater than the signal-to-noise ratio of the energy signal [5]. Although the electromagnetic curve is more cluttered than the energy curve, the characteristics of the data signal are more distinct. In addition, the electromagnetic attack has the advantage that the ability to change the position information can be clarified. This geometric degree of freedom is very useful for identifying leaked information of the question point. The strategy for dealing with electromagnetic radiation analysis attacks is similar to the anti-DPA strategy. Infineon's smart card chip can cope well with DEMA attacks.
2.3 failure analysis attack
Integrated circuit chips used as smart card controllers are usually made of silicon wafers. The electrical properties of the silicon wafer will vary with different environmental parameters. For example, the electrical properties of a silicon wafer can react differently to different voltages, temperatures, light intensities, ionizing radiation, etc., and can also be affected by electromagnetic fields. By changing the environmental parameters, the attacker attempts to induce failure behavior, including the program flow error of the smart card controller. Currently. More attackers are concerned with the so-called DFA (differential fauh attacks), which generate false results by scrambling the encryption system, and these error results can be used to derive the required keys. In the worst case, a simple invalidation operation is enough for the attacker to derive the complete key. The failure analysis attack methods mainly include the following methods:
(1) Spike surge attack in a variety of failure analysis attack methods. The simplest and most widely used method over the years has been to modify the signal input or power supply of the smart card controller. The satellite TV black card that is widely available on the market is cracked by this method (Fig. 4). The instantaneous energy pulse in the power supply is called the surge Spike; the so-called Glitch spike is defined as a special modification to the clock signal. Since both the power supply and the clock signal are required for the operation of the smart card controller, spikes and surge attacks can cause controller failure, ie some electronic modules will temporarily fail, so the wrong operation will be skipped or implemented.
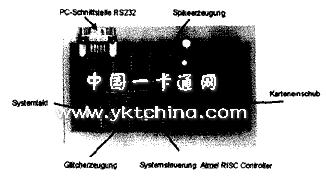
Figure 4 spike surge attack board
(2) Electromagnetic Attacks Although spikes and surge attacks can achieve some effects, more sophisticated methods have been able to incorporate voltage and signal changes into semiconductor chips. For example, a PIN attack on a GSM SIM card allows an attacker to analyze the protected data in the card without having to know the PIN code. In order to inject the disturbed signal into the smart card. Frequent use of electromagnetic coils, it is necessary to put it directly on the surface of the chip. Although the electromagnetic attack is more complicated, compared with the traditional spike or surge attack method, a significant improvement is that the smart card can be placed on a special module for local attack. This makes the corresponding prevention strategy more difficult to develop. If a safety controller can monitor its external supply voltage, it can detect some spikes and surges. But if an electromagnetic pulse is added to a dedicated module, such as a cryptographic coprocessor. It is difficult to be monitored.
Enamel Cookware set is very popular in the family, prepare a gour meal for the whole family with this efcookware's 11 pieces complete cook and bakeware set that blends design with impeccable functionality and versatility.
EF cookware 7 pieces Enameled Cast Iron Cookware set is conducts and retains heat while withstanding the rigors of daily use. Porcelain enamel interior finish requires no seasoning and resists scratches and chips.
EF cookware 6 piece enamel cookware set is colorful and stylish cookware set elegantly present the warmth and care that goes into prepare a meal. The 6 piece cookware set is evenly conduct and retain heat while withstanding the rigors of daily use. Porcelain enamel interior finish require no seasoning and resists scratches and chips.
Enamel Cookware Sets,7 Pieces Enamel Cookware Set,Camping Enamel Cookware Set,Outdoor Enamel Cookware Set
Shijiazhuang Ever Fresh Trading Co., Ltd. , https://www.efhomedeco.com